Featured Products
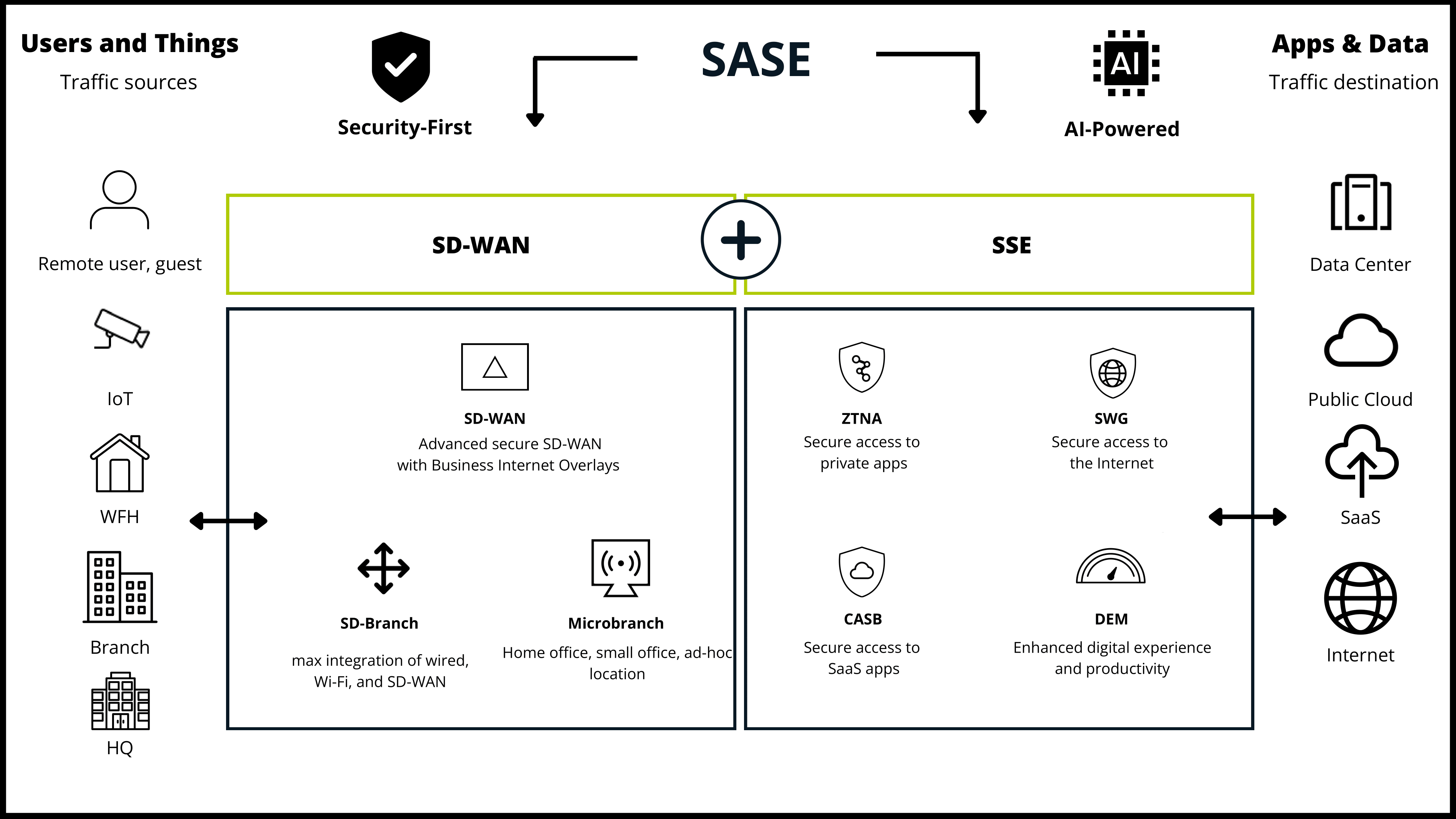
HPE Aruba Networking SSE
HPE Aruba Networking SSE is a secure connectivity platform that elegantly integrates ZTNA, SWG, CASB and DEM into a single, easy-to-use interface, enabling:
-
Secure access for all users (employees, third-party, customers)
-
Secure access from any device (managed, BYOD)
-
A Strategic Partnership
-
Secure access for all applications (private, SaaS, internet)

Kaspersky Next EDR
Level up your security with EDR solutions
-
Advanced endpoint protection
-
Flexible management dashboard
-
Industry-proven anti-ransomware
-
Root Cause Analysis
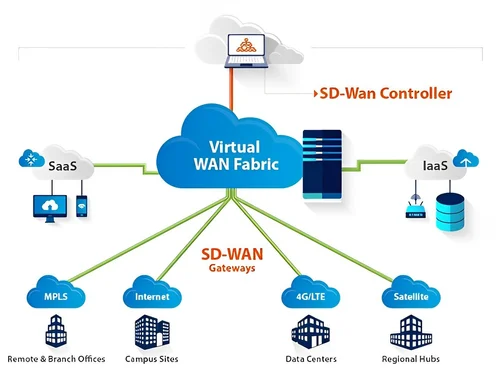
Fortinet Secure SD-WAN
-
FortiGate delivers fast, scalable, and flexible Secure SD-WAN on-premises and in the cloud.
-
Fortinet Secure SD-WAN supports cloud-first, security-sensitive, and global enterprises
-
Fortinet Secure SD-WAN supports the hybrid workforce.

Veeam Backup for Microsoft 365
All‑in‑one backup service delivered by Veeam
-
Experience trusted, comprehensive Microsoft 365 Backup
-
flexible management dashboard
-
Industry-proven anti-ransomware
-
Root Cause Analysis
-
Advanced Security
A next-generation firewall built for the modern, encrypted internet provides industry-leading protection and performance.
-
Streamlined Connectivity
Comprehensive SD-WAN capabilities allow you to securely and efficiently link all of your offices and locations.
-
More Than Just a Firewall
This solution goes beyond basic protection to offer powerful networking tools for a secure and connected enterprise.

Frequently Asked Questions
What are the most common cybersecurity threats to my business?
The most frequent threats businesses face are not always technical hacks. They often rely on human error. The most common attacks include:
- Phishing: This is a social engineering attack where a criminal sends fraudulent emails, texts, or calls to trick employees into revealing sensitive information like login credentials or financial details.
- Malware & Ransomware: Malware is malicious software designed to damage or disrupt computer systems. A particularly dangerous type is ransomware, which encrypts a company’s files and holds them hostage until a ransom is paid.
- Weak Passwords & Account Takeovers: A surprising number of breaches occur because of easily guessed or reused passwords. Once a single account is compromised, attackers can use it to access other parts of the network.
How can I protect my business from these threats?
Cybersecurity is not a one-time effort; it’s a layered strategy. The most effective defenses involve a combination of technology, processes, and people:
- Employee Training: Since most attacks target employees, regular security awareness training is crucial. Teach your staff how to spot a phishing email, create strong passwords, and understand your company’s security policies.
- Multi-Factor Authentication (MFA): This is one of the single most effective security measures. It requires a second form of verification (like a code from your phone) in addition to a password, making it much harder for a hacker to access an account.
- Regular Software Updates: Keep all software, operating systems, and security tools updated. Updates often include critical security patches that close vulnerabilities hackers can exploit.
Do I need a full-time cybersecurity team? What if I'm a small business?
Not necessarily. While large enterprises have dedicated security teams, small and medium-sized businesses can get robust protection in other ways:
- Managed Security Service Provider (MSSP): An MSSP is a third-party company that provides outsourced security monitoring and management services. They can act as your virtual security team, handling everything from threat detection to incident response.
- Cloud Security Services: Many cloud platforms (like AWS, Azure, and Google Cloud) offer built-in security services that automate protection, monitoring, and compliance.
- Employee Roles: If you cannot outsource, designate a key employee to be responsible for implementing and overseeing basic security practices, ensuring backups are done, and enforcing policies.
What should I do if my business experiences a cyberattack?
Having a plan in place is key. A good Incident Response Plan includes these steps:
- Isolate the Threat: Immediately disconnect affected devices or systems from the network to prevent the attack from spreading.
- Contact a Professional: Get help from a cybersecurity firm to investigate the incident, identify the root cause, and contain the damage.
- Communicate: Notify relevant stakeholders, including employees, customers, and partners, about the breach, what happened, and what is being done.
- Learn and Recover: After the incident is resolved, analyze what went wrong and strengthen your defenses to prevent a similar attack in the future.
What is the difference between an Endpoint Security Platform (EPP) and Endpoint Detection and Response (EDR)?
Customers often get confused by the different acronyms used for endpoint protection.
- An Endpoint Protection Platform (EPP), like Sophos Intercept X or Kaspersky Endpoint Security, is a first line of defense. It’s a preventive solution that uses traditional antivirus and anti-malware techniques, along with firewalls and web filters, to stop known threats and block malicious files.
- Endpoint Detection and Response (EDR) is a more advanced technology that monitors a device’s activity in real time. It’s designed to detect sophisticated, unknown threats that EPP might miss, like fileless malware or zero-day exploits. EDR provides the ability to investigate and respond to a threat after it has breached the initial defense, and often includes features to roll back changes caused by a breach.
How does a firewall like FortiGate or H3C protect my network, and do I need other products?
A Next-Generation Firewall (NGFW), like Fortinet’s FortiGate or H3C’s SecPath, is the central pillar of network security. It does more than just block traffic based on IP addresses; it performs deep packet inspection to analyze the content of network traffic, identifies and blocks applications, and can detect and prevent intrusions.
However, a firewall on its own is not enough. Customers are advised to implement a layered security strategy. Modern solutions from these vendors are designed to be part of a larger ecosystem, such as the Fortinet Security Fabric. This fabric integrates the firewall with other security products like endpoint protection, sandboxing, and network management tools to create a unified and centrally managed defense.
Why are security vulnerabilities constantly being found, and how do I keep up with patches?
Customers of major vendors, particularly Fortinet, are concerned about the frequent discovery of new vulnerabilities. These are not a sign of poor products but rather an indication of how complex and large modern software is. Patches are essential to address these vulnerabilities and are released to protect customers before attackers can exploit them.
To keep up, customers are advised to:
- Subscribe to vendor security bulletins and alerts (e.g., Fortinet’s FortiGuard Labs or SophosLabs).
- Use a centralized management platform (like FortiManager or Sophos Central) that allows them to push updates and patches to all devices at once.
- Have a proactive plan for regular updates, rather than waiting for an incident. A robust patching schedule is a critical part of maintaining a secure network.
Can I manage all my security products from a single console?
This is a key question for customers. The answer is a definitive yes, and it is a major selling point for all of the major vendors. The concept is known as a unified security platform or centralized management.

